Relay Vs Switch
A relay is an electrically operated switch. Current flowing through the coil of the relay creates a magnetic field which attracts a lever and changes the switch contacts. The coil current can be on or off so relays have two switch positions and they are double throw (changeover) switches.
Relays allow one circuit to switch a second circuit which can be completely separate from the first. For example a low voltage battery circuit can use a relay to switch a 230V AC mains circuit. There is no electrical connection inside the relay between the two circuits; the link is magnetic and mechanical.
The coil of a relay passes a relatively large current, typically 30mA for a 12V relay, but it can be as much as 100mA for relays designed to operate from lower voltages.
Most ICs (chips) cannot provide this current and a transistor is usually used to amplify the small IC current to the larger value required for the relay coil. The maximum output current for the popular 555 timer IC is 200mA so these devices can supply relay coils directly without amplification.
Relays are usually SPDT or DPDT but they can have many more sets of switch contacts, for example relays with 4 sets of changeover contacts are readily available. For further information about switch contacts and the terms used to describe them please see the page on switches.
Most relays are designed for PCB mounting but you can solder wires directly to the pins providing you take care to avoid melting the plastic case of the relay.
The supplier's catalogue should show you the relay's connections. The coil will be obvious and it may be connected either way round. Relay coils produce brief high voltage 'spikes' when they are switched off and this can destroy transistors and ICs in the circuit. To prevent damage you must connect a protection diode across the relay coil.
The animated picture shows a working relay with its coil and switch contacts.
You can see a lever on the left being attracted by magnetism when the coil is switched on. This lever moves the switch contacts. There is one set of contacts (SPDT) in the foreground and another behind them, making the relay DPDT.
The relay's switch connections are usually labeled COM, NC and NO:
• COM = Common, always connect to this,it is the moving part of the switch.
• NC = Normally Closed,
COM is connected to this when the relay coil is off.
• NO = Normally Open, COM is connected to this when the relay coil is on.
• Connect to COM and NO if you want the switched circuit to be on when the relay coil is on.
• Connect to COM and NC if you want the switched circuit to be on when the relay coil is off.
Choosing a relay
You need to consider several features when choosing a relay:
1. Physical size and pin arrangement
If you are choosing a relay for an existing PCB you will need to ensure that its dimensions and pin arrangement are suitable. You should find this information in the supplier's catalogue.
2. Coil voltage
The relay's coil voltage rating and resistance must suit the circuit powering the relay coil. Many relays have a coil rated for a 12V supply but 5V and 24V relays are also readily available. Some relays operate perfectly well with a supply voltage which is a little lower than their rated value.
3. Coil resistance
The circuit must be able to supply the current required by the relay coil. You can use Ohm's law to calculate the current:
Relay coil current = supply voltage
coil resistance
4. For example: A 12V supply relay with a coil resistance of 400 passes a current of 30mA. This is OK for a 555 timer IC (maximum output current 200mA), but it is too much for most ICs and they will require a transistor to amplify the current.
5. Switch ratings (voltage and current)
The relay's switch contacts must be suitable for the circuit they are to control. You will need to check the voltage and current ratings. Note that the voltage rating is usually higher for AC, for example: "5A at 24V DC or 125V AC".
6. Switch contact arrangement (SPDT, DPDT etc)
Most relays are SPDT or DPDT which are often described as "single pole changeover" (SPCO) or "double pole changeover" (DPCO). For further information please see the page on switches.
Protection diodes for relays
Transistors and ICs (chips) must be protected from the brief high voltage 'spike' produced when the relay coil is switched off. The diagram shows how a signal diode (e.g. 1N4148) is connected across the relay coil to provide this protection. Note that the diode is connected 'backwards' so that it will normally not conduct. Conduction only occurs when the relay coil is switched off, at this moment current tries to continue flowing through the coil and it is harmlessly diverted through the diode. Without the diode no current could flow and the coil would produce a damaging high voltage 'spike' in its attempt to keep the current flowing.
Advantages of relays:
• Relays can switch AC and DC, transistors can only switch DC.
• Relays can switch high voltages, transistors cannot.
• Relays are a better choice for switching large currents (> 5A).
• Relays can switch many contacts at once.
Disadvantages of relays:
• Relays are bulkier than transistors for switching small currents.
• Relays cannot switch rapidly (except reed relays), transistors can switch many times per second.
• Relays use more power due to the current flowing through their coil.
• Relays require more current than many chips can provide, so a low power transistor may be needed to switch the current for the relay's coil.



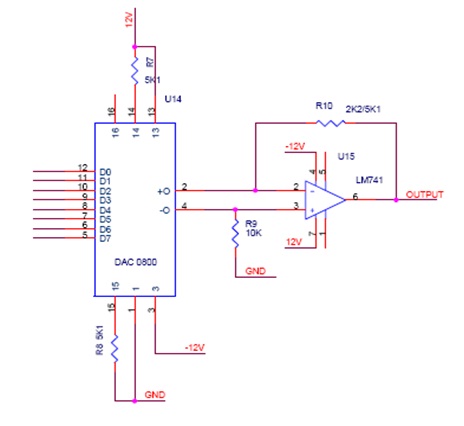

 Logic diagramm
Logic diagramm

 source of image: Wikipedia
source of image: Wikipedia Pin Diagram
Pin Diagram
 RF Transmitter
RF Transmitter
 RS232 Level shifting
RS232 Level shifting









 image from:Wikipedia
image from:Wikipedia


